Setting up a secure computer password isn’t just about meeting basic requirements. It’s your first line of defense against increasingly sophisticated cyber attacks. Most users unknowingly create vulnerable passwords. Hackers can crack these within minutes. This leaves personal data, financial information, and digital identity completely exposed.
This comprehensive guide reveals proven password creation strategies used by cybersecurity professionals. You’ll learn character composition techniques that resist modern attack methods. We cover system-specific setup procedures for Windows, macOS, and Linux.
You’ll discover how to implement advanced security features like biometric authentication and hardware keys. Plus, learn essential password management practices that protect multiple accounts simultaneously.
Understanding Computer Password Basics
Master the fundamentals of computer passwords, including system requirements, security standards, and essential terminology, before diving into advanced protection strategies.
Password Requirements by Operating System
Different operating systems have varying password requirements and security protocols. Windows 10 and 11 typically require passwords to be at least eight characters long, while macOS systems may have different minimum requirements depending on your security settings.
Most modern systems support complex passwords that include uppercase letters, lowercase letters, numbers, and special characters. Understanding your system’s specific requirements helps you create passwords that meet technical standards while maximizing security.
Types of Computer Passwords
Computer systems utilize several password types for different security layers. Your login password protects initial system access, while administrator passwords control system-level changes and software installations.
Some systems also support PIN codes for quick access and biometric authentication as password alternatives. Understanding these options helps you choose the most appropriate security method for your specific needs and usage patterns.
Password Storage Mechanisms
Operating systems store passwords using sophisticated encryption algorithms that convert your password into unreadable code. Windows uses NTLM hashing, while macOS employs keychain encryption to protect stored credentials.
These security mechanisms ensure that even if someone gains access to your computer’s storage, your actual passwords remain protected. Understanding how your system stores passwords helps you appreciate the importance of choosing strong, unique credentials.
Creating Strong Computer Passwords
Learn proven techniques for generating robust passwords that resist common attack methods while remaining manageable for daily use across different computing environments.
Character Composition Strategies
Strong passwords combine multiple character types to create complexity that resists automated attacks. Include uppercase letters, lowercase letters, numbers, and special characters in unpredictable patterns that avoid common substitutions.
Avoid simple character substitutions like replacing “a” with ”@” or “o” with “0,” as these patterns are easily recognized by password-cracking software. Instead, create unique combinations that don’t follow predictable patterns or dictionary words.
Length and Complexity Balance
Password length significantly impacts security strength, with longer passwords providing exponentially better protection. Aim for a minimum 12 characters for basic security, though 16-20 characters offer superior protection against advanced attacks.
Balance complexity with memorability by using passphrases that combine multiple unrelated words with numbers and special characters. This approach creates long, secure passwords that are easier to remember than random character strings.
Avoiding Predictable Patterns
Several common mistakes people make when creating passwords include using personal information, sequential numbers, or keyboard patterns like “qwerty123.” These predictable elements make passwords vulnerable to both automated attacks and social engineering attempts.
Instead, develop passwords using unrelated concepts, random word combinations, or strong password generator tools that create truly random character sequences. This approach eliminates human bias that often leads to predictable password choices.
Password Uniqueness Importance
Each computer and account should have a unique password to prevent credential stuffing attacks, where compromised passwords from one system are used to access other accounts. Password reuse multiplies security risks across your entire digital presence.
Maintain password uniqueness by creating distinct passwords for different systems or using password management tools that generate and store unique credentials automatically. This strategy limits damage if one password becomes compromised.
Setting Passwords on Different Operating Systems
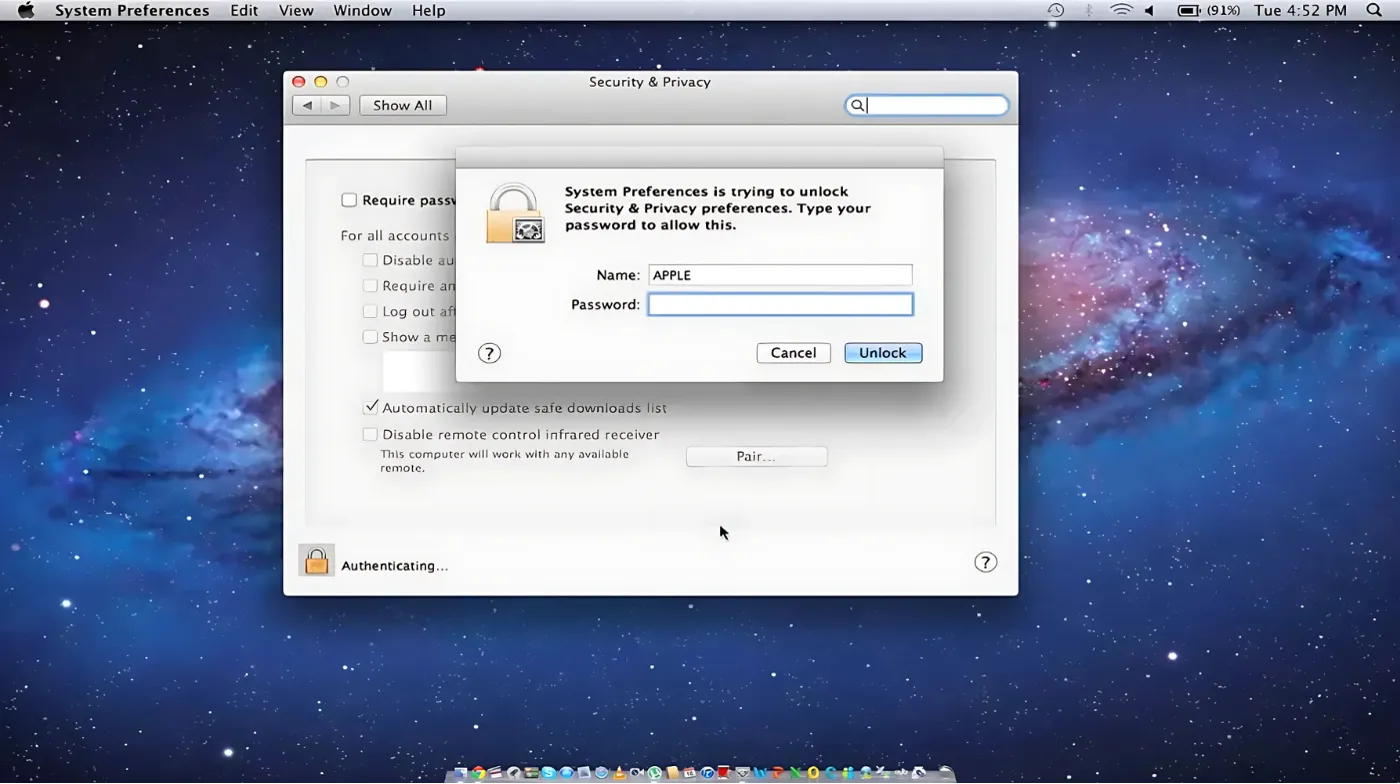
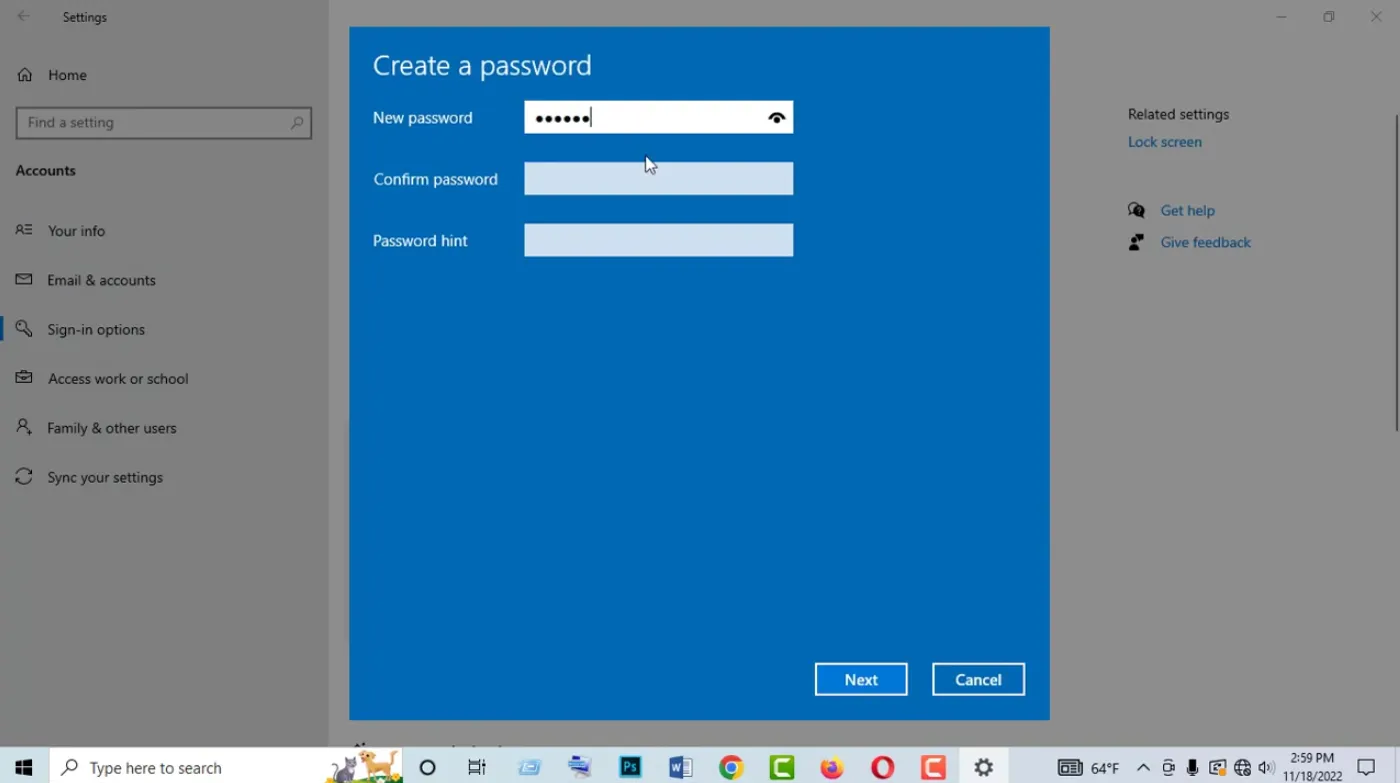
Navigate system-specific password setup procedures with detailed instructions for Windows, macOS, and Linux environments, including security option configurations.
Windows Password Configuration
Windows systems offer multiple password setup methods through Settings or Control Panel interfaces. Access password settings by navigating to Settings > Accounts > Sign-in options, where you can configure passwords, PINs, and biometric authentication.
When creating Windows passwords, ensure they meet complexity requirements, including uppercase letters, lowercase letters, numbers, and special characters. Windows may also require passwords to differ significantly from previous passwords to prevent simple modifications.
macOS Password Setup
macOS password configuration occurs during initial setup or through System Preferences > Users \ Groups. Click the lock icon to make changes, then select your user account to modify password settings.
macOS integrates passwords with Apple ID and iCloud Keychain services, providing seamless synchronization across Apple devices. Consider enabling these features for convenience while understanding their security implications and data sharing aspects.
Configure FileVault encryption alongside password setup to encrypt your entire disk, ensuring that password protection extends to stored data even if someone gains physical access to your computer.
Linux Password Management
Linux systems handle passwords through command-line interfaces and graphical tools, depending on your distribution. Use the “passwd” command to change passwords or access distribution-specific user management tools.
Linux offers extensive password policy configuration through PAM (Pluggable Authentication Modules), allowing detailed control over password requirements, expiration, and security policies. These advanced options provide enterprise-level password management.
Best Practices for Password Management
Implement professional password management strategies, including storage solutions, regular maintenance procedures, and security monitoring techniques for comprehensive protection.
Password Manager Integration
Essential random password generators and password managers provide comprehensive solutions for creating, storing, and managing complex passwords across multiple systems. These tools eliminate the need to remember numerous unique passwords while maintaining security.
Choose reputable password managers that offer cross-platform synchronization, secure sharing capabilities, and advanced features like breach monitoring. Popular options include built-in browser managers and dedicated applications with enhanced security features.
Regular Password Updates
Develop systematic password update schedules based on security requirements and risk assessment. While frequent changes aren’t always necessary, update passwords immediately after security breaches or when leaving shared computer environments.
Monitor security news and breach notifications to identify when specific services or systems may have been compromised. Proactive password updates following security incidents can prevent unauthorized access before attackers exploit stolen credentials.
Regularly check password strength checker tools and security services that evaluate your current passwords against known compromised credential databases. These services help identify potentially vulnerable passwords requiring updates.
Multi-Factor Authentication Integration
Complement strong passwords with multi-factor authentication (MFA) wherever possible to create layered security that protects against password-based attacks. MFA significantly enhances security even if passwords become compromised.
Configure authentication apps, SMS verification, or hardware tokens as second factors for your most critical systems. This additional security layer protects against unauthorized access even when passwords are known to attackers.
Balance security with usability when implementing MFA, choosing methods that provide strong protection without creating excessive friction for daily computer use. Consider trusted device settings for frequently used systems.
Advanced Password Security Features

Explore cutting-edge password security technologies, including biometric authentication, hardware keys, and enterprise-grade protection systems for maximum security.
Biometric Authentication Options
Modern computers increasingly support biometric authentication methods, including fingerprint readers, facial recognition, and voice authentication as password alternatives or supplements. These technologies provide convenient access while maintaining security.
Configure biometric authentication as a secondary option rather than a complete password replacement, ensuring you retain access if biometric systems fail or become unavailable. Maintain traditional password access for troubleshooting scenarios.
Hardware Security Keys
Hardware security keys provide physical two-factor authentication that significantly enhances password security. These devices generate unique authentication codes or use cryptographic protocols that resist digital attacks completely.
Popular hardware key standards include FIDO2 and U2F protocols that integrate with major operating systems and web services. These standardized approaches ensure compatibility across different platforms and services.
Consider backup hardware keys and recovery procedures when implementing physical security devices. Having multiple keys prevents lockout situations if primary keys are lost or damaged.
Enterprise Security Policies
Organizations often implement centralized password policies that enforce consistent security standards across all systems and users. These policies may include complexity requirements, expiration schedules, and authentication protocols.
Group Policy settings in Windows domains or similar management tools in other environments allow administrators to enforce password standards automatically. Understanding these policies helps users comply with organizational security requirements.
Frequently Asked Questions
How often should I change my computer password?
Change your computer password when security breaches occur, when sharing computer access ends, or when you suspect unauthorized access. Modern security practices favor strong, unique passwords over frequent changes unless specific threats arise.
What makes a computer password strong enough?
Strong computer passwords contain at least 12-16 characters with uppercase letters, lowercase letters, numbers, and special characters in unpredictable patterns. Avoid personal information, dictionary words, and common substitution patterns that attackers easily guess.
Securing Your Digital Future with a Strong Computer Password
Setting secure computer passwords represents a fundamental step in protecting your digital life from evolving cyber threats. By implementing strong password creation techniques, utilizing proper management tools, and maintaining good security hygiene, you create robust defenses against unauthorized access and data breaches.
Remember that password security extends beyond initial setup to include ongoing maintenance, monitoring, and adaptation to new threats. Regular security audits, breach monitoring, and password updates ensure your protection remains effective over time.
Take action today by implementing these password security strategies across all your computing devices. Your proactive approach to password security creates a foundation for comprehensive digital protection that safeguards your personal information, professional data, and online privacy.
